|
| Social Media Examples |
| |
|
| |
| The table below provides links to materials which are relevant and applicable across all of the courseware in this program. For ease of access, this table is reproduced on every page of each lesson. |
| |
|
| |
|
| |
| This module uses the framework for analysis to analyze several of the popular social media sites. While an extensive analysis of all of the social media applications would be prohibitive, these sites are particularly important. In total, these sites have hundreds of millions of users. |
| |
| LinkedIn |
 |
| Analysis of LinkedIn |
| Identification | Name: LinkedIn
URL: www.linkedin.com |
| Application | Professional networking. Reconnects past colleagues and acquaintances. Job search and career development. Subject expertise finding. |
| Personal identity | Professional. |
| Evolved organization | Through search users "find" other users/groups/organizations who they would like to be affiliated with. The users messages the other user/group/organization. The other user or a responsible individual at the group/organization approves the connection and a link is established. |
| Lurking | Limited information about the member is available publicly. |
| Persistence | Profiles, links, content, history and other information. Libraries of resources. |
| Membership | Anyone with a valid email address can become a member. No fees are charged. |
| Roles | All members are equal. Groups and organizations have managers. |
| Funding | Organizations pay services fees , advertising |
| Interaction | Users have a built-in messaging capability. Groups and organizations support discussion lists. |
| Sanctions | Users can refuse to link to others. Users can unlink from undesirable users. LinkedIn can terminate a misbehaving user's account. |
|
| |
LinkedIn Traffic Stimulation eMail Message Examples
- Hi Ken, I'd like to join your LinkedIn network.
- 64 Notifications and updates from your network
25+ new updates
15 invitations
3 job changes
7 messages
- ***** ***** has 6 new connections
- ***** ***** invited you to connect 7 days ago.
- You appeared in 8 searches this week
- You were found by people from these companies
- ***** ***** -We are HIRING would like to connect on LinkedIn. How would you like to respond?
- You and Ronald have 3 mutual connections in common.
- Ken, it's been a while since you last signed in to LinkedIn.
- Congratulate **** on a work anniversary.
- Connect with other people at Pitt.
|
| |
| Exercise: |
- If you don't already have one, create an account on LinkedIn www.linkedin.com.
- Create a profile for yourself.
- Send me (sochats@pitt.edu) an invitation to connect to you.
- Explore some of the features of LinkedIn on your own.
|
|
| |
|
| |
| eBay |
 |
| |
| Analysis of eBay |
| Identification | Name: eBay
URL:www.ebay.com |
| Application | eBay is a marketplace broker. It creates permanent markets, called Stores, and on-line auctions |
| Personal identity | My eBay is a home for all transactions, preferences and other personal data for a user. |
| Evolved organization | Users have organized themselves into hundreds of categories from Antiques to Toys. Specialized marketplaces for items such as real estate, vehicles and other items have evolved. |
| Lurking | Anyone can view an auction or browse a store. |
| Persistence | Complete histories for buyers, sellers and goods. | |
| Membership | Users need to have an account (bank, credit, PayPal, etc.) which can be charged |
| Roles | Buyer or seller. There are multiple classes fo sellers based on user feedback. |
| Funding | Transaction fees, advertizing |
| Interaction | Sellers offer goods for sale and buyers bid on them. |
| Sanctions | Based on user feedback sellers may be banished. Individual items may be withdrawn. |
|
| |
| Examples of emergency management items found on eBay:
Fire Trucks
ambulances
Face Masks
Face Mask Cartridges
Fire Extinguisher
Bunker Gear
Bulletproof Vests
Hazmat
Medical Supplies/Equipment
Police
Naloxone
|
| |
|
| |
| WikipediA |
 |
| Analysis of Wikipedia |
| Identification | Name: WikipediA
URL:www.wikipedia.org |
| Application | Online user-edited encyclopedia. |
| Personal identity | Editors have accounts. |
| Evolved organization | Terms are linked by usage and reference. |
| Lurking | Anyone can read WikipediA |
| Persistence | Historiees of edits are kept. |
| Membership | Anyone can create an account. |
| Roles | Users are readers or editors. |
| |
| Interaction | Any term may be updated at any time. |
| Sanctions | Misbehavine users caan be banished from the ssite. |
|
| |
|
|
| |
|
I had done a book about Albert Einstein and noticed that the Wikipedia entry on him claimed that he had traveled to Albania in 1935 so that King Zog could help him escape the Nazis by getting him a visa to the United States. This was completely untrue, even though the passage included citations to obscure Albanian websites where this was proudly proclaimed, usually based on some third-hand series of recollections about what someone’s uncle once said a friend had told him. I deleted the assertion from the article, only to watch it reappear.
|
| |
|
On the discussion page, I provided sources for where Einstein actually was during the time in question (Princeton) and what passport he was using (Swiss). But tenacious Albanian partisans kept reinserting the claim. The Einstein-in-Albania tug-of-war lasted weeks. I became worried that the obstinacy of a few passionate advocates could undermine Wikipedia’s reliance on the wisdom of crowds. But after a while, the edit wars ended, and the article no longer had Einstein going to Albania.
|
| |
Example searches on WikimediA
- University of Pittsburgh
- Chick-fil-A
- Hobby Lobby
- Vaccine
|
| |
|
| |
| |
| Facebook |
 |
| Analysis of Facebook |
| Identification | Name: Facebook
URL:www.facebook.com |
| Application | Social Networking |
| Personal identity | Users have named accounts. Organizations and groups can have accounts. |
| Evolved organization | By linking to each other, users form a social network. Users can determine who can link to them and what may be shown/shared. |
| Lurking | Limited. |
| Persistence | All data about a user/organization/group is maintained. |
| Membership | None. |
| Roles | All user entities essentially are the same and equal. |
| Funding | Fees and advertising, sales of data |
| Interaction | Users can link, message and email each other. |
| Sanctions | Misbehaving users can be banished from the site. Individual users can unlink to other users. |
|
| |
| Facebook has had many problems with regulators in the United States and other countries, particularly the European Union.
Most of these problems have centered around the protection of the private data of users, advertising policies and antitrust behavior.
See for example: FTC Consent Decree. |
| |
| A congressional commitee is currently investigating the behavior of social media firms. The CEOs of Facebook, Twitter, amazon and others have been called to testify. |
| |
In 2020, FTC Sues Facebook for Illegal Monopolization See FTC site.
Participating Attorneys General include: Alaska, Arizona, Arkansas, California, Colorado, Connecticut, Delaware, the District of Columbia, Florida, Guam, Hawaii, Idaho, Illinois, Indiana, Iowa, Kansas, Kentucky, Louisiana, Maine, Maryland, Massachusetts, Michigan, Minnesota, Mississippi, Missouri, Montana, Nebraska, Nevada, New Hampshire, New Jersey, New Mexico, New York, North Carolina, North Dakota, Ohio, Oklahoma, Oregon, Pennsylvania, Rhode Island, Tennessee, Texas, Utah, Vermont, Virginia, Washington, West Virginia, Wisconsin, and Wyoming. |
| |
Interestingly, law enforcement has become increasingly interested in using social media as a tool. The criminal culture is one that often lives outside the mainstream. They don't get married, register to vote, get a drivers' license or behave in ways which would create data on them.
However, because of the machismo culture of gangs, illlegals and others, they regularly post information which aids in their apprehension.
Some examples include:
- Street Names (e.g. Smoke, TayTay, Little Man, etc.)
- Relationships (baby daddy, baby mama)
- Accomplices (peeps)
- Pictures
- Tatoos
- Piercings
- Teeth (gold, diamonds, missing)
- Hair (dreads, colors, afros, mullets)
- Jewelry (bling)
- Clothes (colors)
- Cars
- Weapons
- Drugs
- Brags about crimes
Some examples of law enforcement use of social and other media include:
- A drug deal that went bad occurred on a crowded street in New Orleans, Louisiana. A gun battle erupted between the buyers and sellers. Four shooters were involved. Five innocent bystanders were killed and injured. One of the shooters was identified by a witness. Street cameras caught some of the action, but as it was evening, the images wer fuzzy. The NOPD looked up the identified perpetrator on Facebook and discoverd a picture of the suspect with his arms around his two unidentified accomplices. Their names were given in the picture tagline. All three were convicted of murder.
- Tulsa, Oklahoma police were able to identify the body of a badly burned corpse through the tatoo on an arm of the victim that was not burned. That identification led to the conviction of his murderer.
-
In Iowa City, Iowa a teenage girl was attacked and murdered outside a local mall. DNA evidence was recovered from underneath her fingernails. The local police submitted the evidence to the
CODIS system (Combined DNA Index System) CODIS maintained by the FBI. The search resulted in no hits. The police then tried a search on an ancestry service. The result was a familial match to a woman living in Oregon. It was discovered that the woman prviously lived in Iowa City and had three sons who were still living in the area. A court order was issued compelling each of the three sons to submit a DNA sample. One of the sons was a match and was subsequently convicted of the murder.
- In Texas a man was murdered in his hot tub. On a stand next to the hot was an Amazon Alexa. The district attorney issued an order to produce any recordings from the device. Amazon was not forthcoming.
|
| |
| Facebook has been associated with many crimes. See www.robertreeveslaw.com.
|
| |
|
| |
| Twitter |
 |
| Analysis of Twitter |
| Identification | Name: Twitter
URL:www.twitter.com |
| Application | Social network messaaging. |
| Personal identity | Named account. |
| Evolved organization | Users "follow" other users by attaching themselves to that user's tweet stream. |
| Lurking | Tweets are public by default. |
| Persistence | Profiles and tweet history. |
| Membership | Accounts with profiles. |
| Roles | Tweeteer and follower. |
| |
| Interaction | Users send 140 character messages (tweets). |
| Sanctions | Users can have their accounts disabled. Users can "unfollow" users. |
|
|
| |
| YouTube |
 |
| Analysis of YouTube |
| Identification | Name: YouTube
URL:www.youtube.com |
| Application | Video sharing library. |
| Personal identity | Through registration users create profiles. |
| Evolved organization | Search engines categorize videos. |
| Lurking | Unregistered users can watch videos. |
| Persistence | Huge video library. |
| Membership | None. |
| Roles | Publishers and viewers. |
|
| www.youtube.com |
Sample Videos
Emergency Videos
|
|
| |
| Second Life |
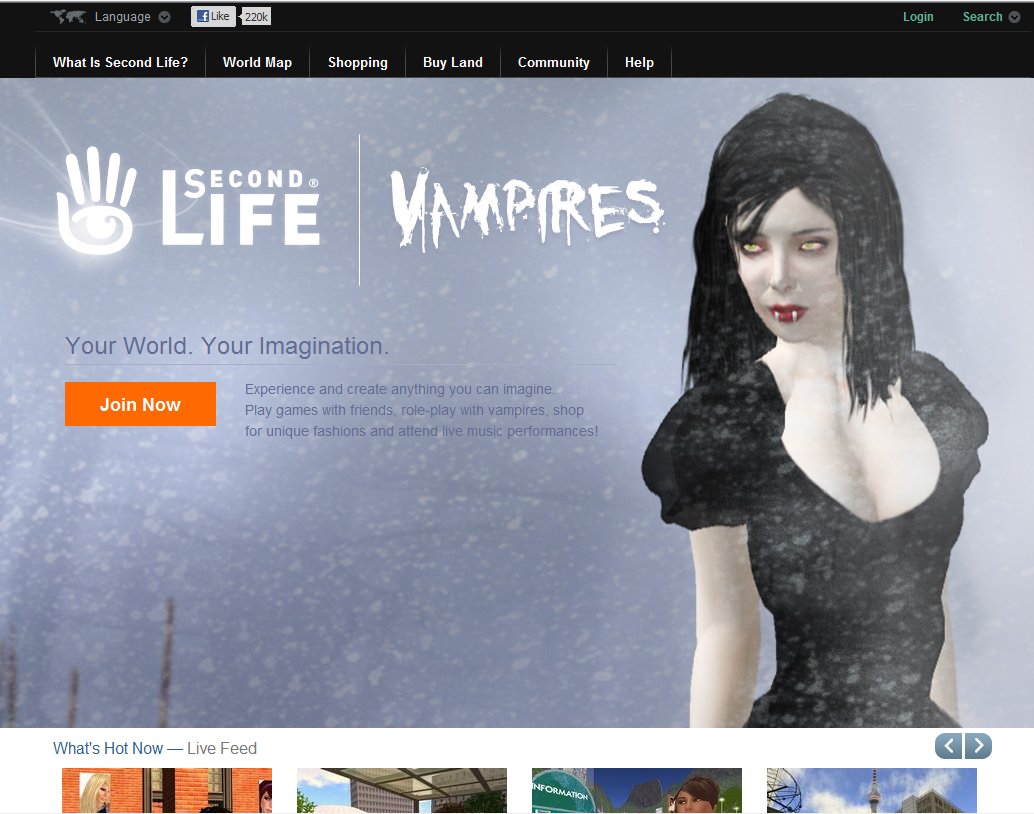 |
| Analysis of Second Life |
| Identification | Name: Second Life
URL:www.secondlife.com |
| Application | Virtual reality experimental world. |
| Personal identity | Users are represented by avatars and their characteristics. |
| Evolved organization | User determined. Real estate, commerce, goods, events, etc. have evolved. |
| Lurking | Not permitted |
| Persistence | The world is maintained on linked servers. |
| Membership | What are the prerequisites for membership/participation |
| Roles | User roles are self defined. Users can be animals if they want. |
| Interaction | Avatars can interact much as humans. |
| Sanctions | There are no rules in Second Life. |
|
| |
| Avatars |
| |
  Ken's Avatars Ken's Avatars |
| |
 
|
| |
 
|
| |
 Animal Avatars Animal Avatars |
| |
 Vehicle Avatars Vehicle Avatars |
| |
 Robot Avatars Robot Avatars |
| |
 Vampire Avatars Vampire Avatars |
| |
| Environments |
| |
 Fantasy World Fantasy World |
| |
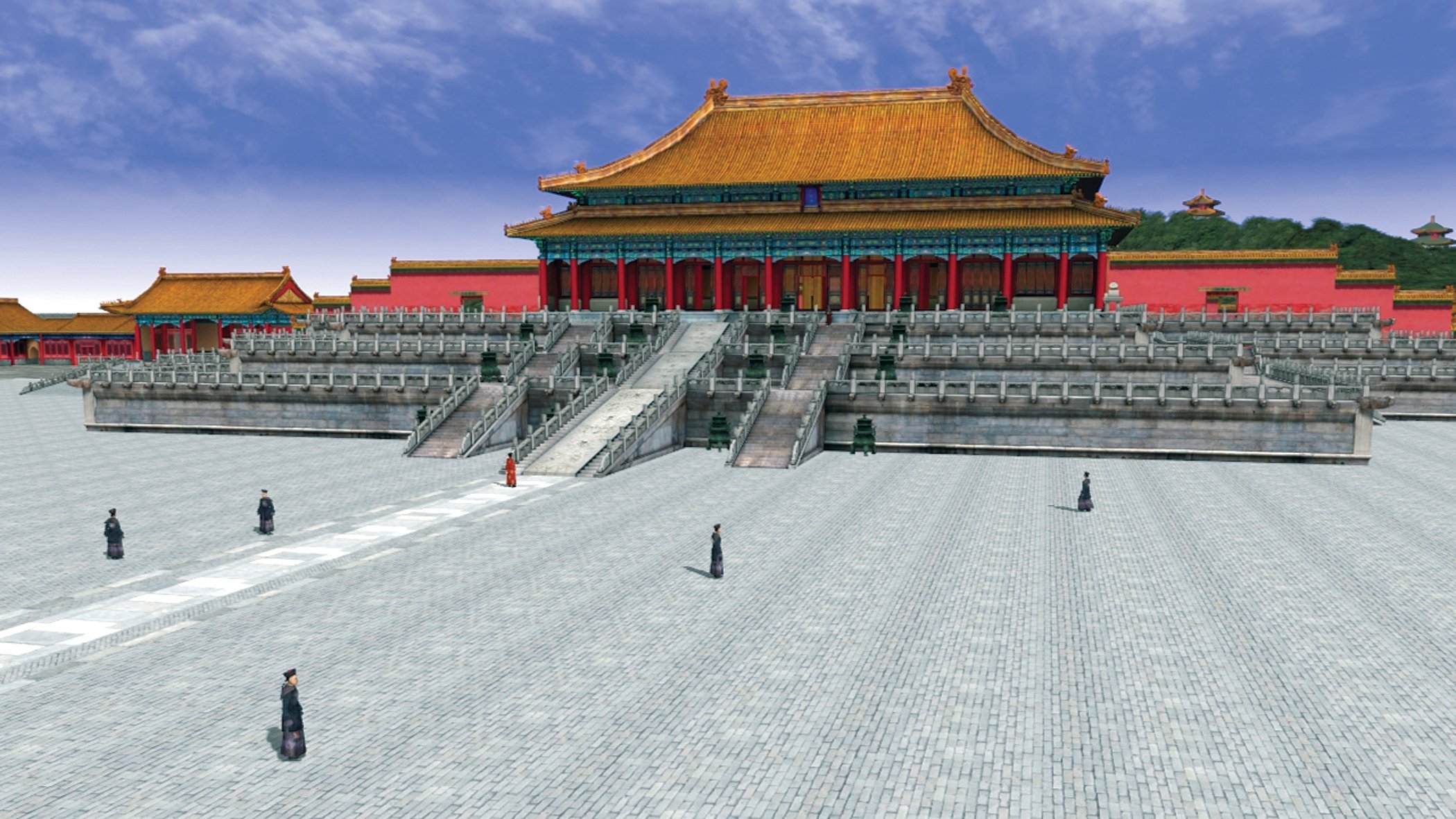 Forbidden Palace Forbidden Palace |
| |
 Forbidden Palace Courtyard Forbidden Palace Courtyard |
| |
 Forbidden Palace Interior Forbidden Palace Interior |
| |
 IBM Training Facility IBM Training Facility |
| |
 Jet Propulsion Laboratories Jet Propulsion Laboratories |
| |
 Texas A&M Texas A&M |
| |
 Nottingham University Nottingham University |
| |
 Virtual Classroom Virtual Classroom |
| |
| Second Life Marketplace marketplace.secondlife.com |
| |
| Buildings |
| |
 Gothic Watchtower - L$2950 Gothic Watchtower - L$2950 |
| |
 Contemporary House - L$1450 Contemporary House - L$1450 |
| |
| Clothes |
| |
 Kerry Heels - L$299 Kerry Heels - L$299 |
| |
 Larry Jeans - L$99 Larry Jeans - L$99 |
| |
 Pregnant Dress - L$55 Pregnant Dress - L$55 |
| |
 Cropped Hoodie - L$1 Cropped Hoodie - L$1 |
| |
 Second Life Class Group Assignment Second Life Class Group Assignment |
| |
| Second Life Problems |
| |
Second Life has experienced a number of problems that we encounter in First Life including but not limited to:
- Sex
- Vices
- Murder
- Crime
- Riots
|
|
| |
| Delicious |
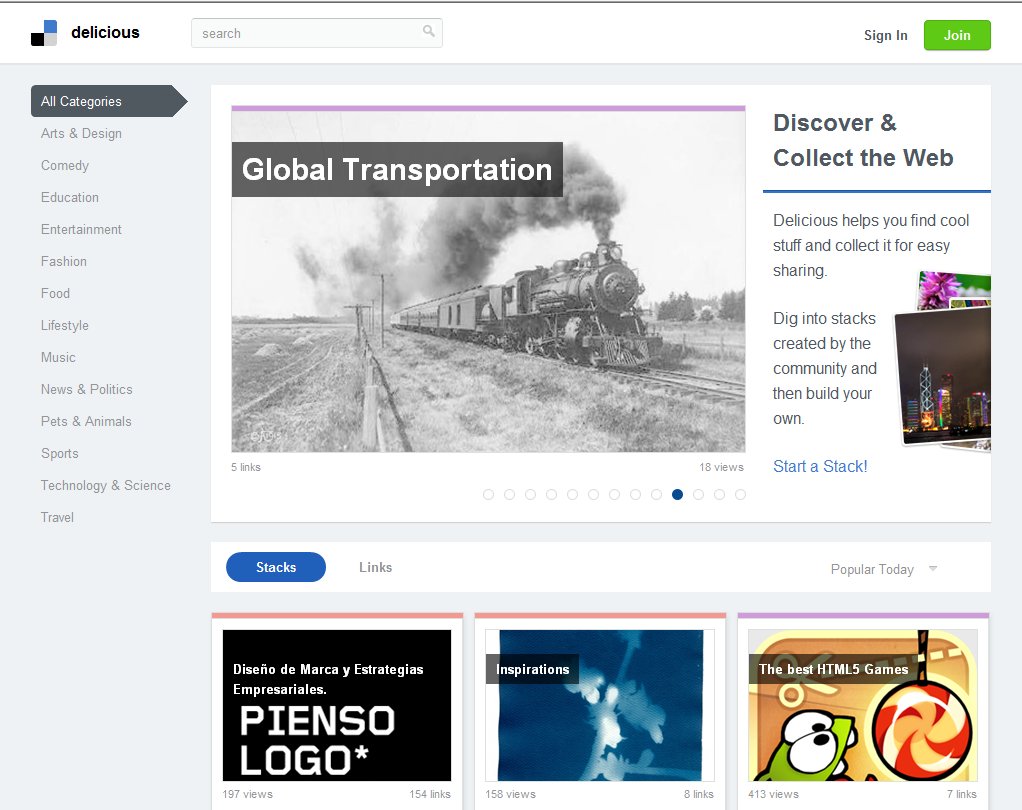 |
| Analysis of Delicious |
| Identification | Name: Delicious
URL:www.delicious.com |
| Application | Web site recommending and popularity. |
| Personal identity | Accounts. |
| Evolved organization | Categorized topics that evolve via user input.. |
| Lurking | Permitted. |
| Persistence | Indexes of popular web sites. |
| Membership | Open. |
| Roles | Readers and Recommenders. |
| Interaction | Users read the recommended links of others. |
| Sanctions | Misbehaving users may lose their priviledges. |
|
|
| |
| Digg |
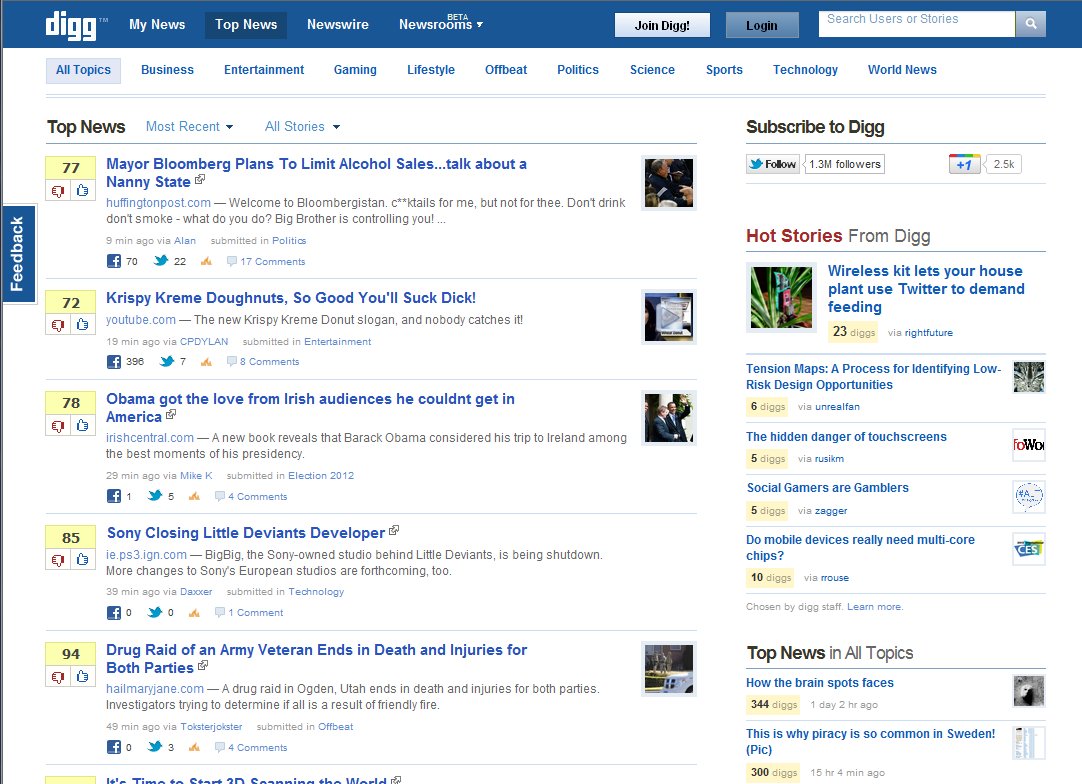 |
| Analysis of Digg |
| Identification | Name: Digg
URL:www.digg.com |
| Application | Social news and commentary. |
| Personal identity | Accounts. |
| Evolved organization | User directed indexing. |
| Lurking | Permitted. |
| Persistence | Indexes of popular news items. |
| Membership | Open. |
| Roles | Readers and Posters. |
| Interaction | Users read the recommended links of others. |
| Sanctions | Misbehaving users may lose their priviledges. |
|
| |
|
| Notice the graphics and organization of these web sites. High quality graphics are used to create a "home". |
|
| Exercise: |
Use the analysis framework to analyze the social media site Trapster: www.trapster.com. |
|
| |
|
|
|
|
| Copyright © 2011, 2024 Ken Sochats |









 Fantasy World
Fantasy World Forbidden Palace
Forbidden Palace Forbidden Palace Courtyard
Forbidden Palace Courtyard Forbidden Palace Interior
Forbidden Palace Interior IBM Training Facility
IBM Training Facility Jet Propulsion Laboratories
Jet Propulsion Laboratories Texas A&M
Texas A&M Nottingham University
Nottingham University Virtual Classroom
Virtual Classroom Gothic Watchtower - L$2950
Gothic Watchtower - L$2950 Contemporary House - L$1450
Contemporary House - L$1450 Kerry Heels - L$299
Kerry Heels - L$299 Larry Jeans - L$99
Larry Jeans - L$99 Pregnant Dress - L$55
Pregnant Dress - L$55 Cropped Hoodie - L$1
Cropped Hoodie - L$1 Second Life Class Group Assignment
Second Life Class Group Assignment